Unveiling SSL Decryption: Enhancing Network Security with Palo Alto Firewall
SSL Decryption is still a bit mysterious with what it is, how it works and what it’s used for. Let this blog be your guide so your SSL Decryption journey goes smoothly! In this blog post, we'll explore SSL decryption on a Palo Alto Firewall, providing step-by-step guidance on how to implement this crucial security feature effectively.
In the realm of cybersecurity, SSL encryption has become ubiquitous, safeguarding sensitive data transmitted over the internet. However, while SSL encryption protects data from prying eyes, it also poses a challenge for network security professionals, as encrypted traffic can conceal malicious activity. Palo Alto Networks Next-Generation Firewalls (NGFWs) offer a powerful solution to this challenge through SSL decryption.
Understanding SSL Decryption
You can’t protect what you can’t see. SSL decryption is a process by which encrypted SSL/TLS traffic is intercepted, decrypted, inspected for threats, and then re-encrypted before reaching its destination. By decrypting SSL traffic, organizations can effectively enforce security policies, detect and prevent threats hidden within encrypted communication, and ensure regulatory compliance without compromising privacy.
Implementing SSL Decryption on a Palo Alto NGFW
Step 1: Enable SSL Decryption
Log in to the Palo Alto Networks NGFW web interface.
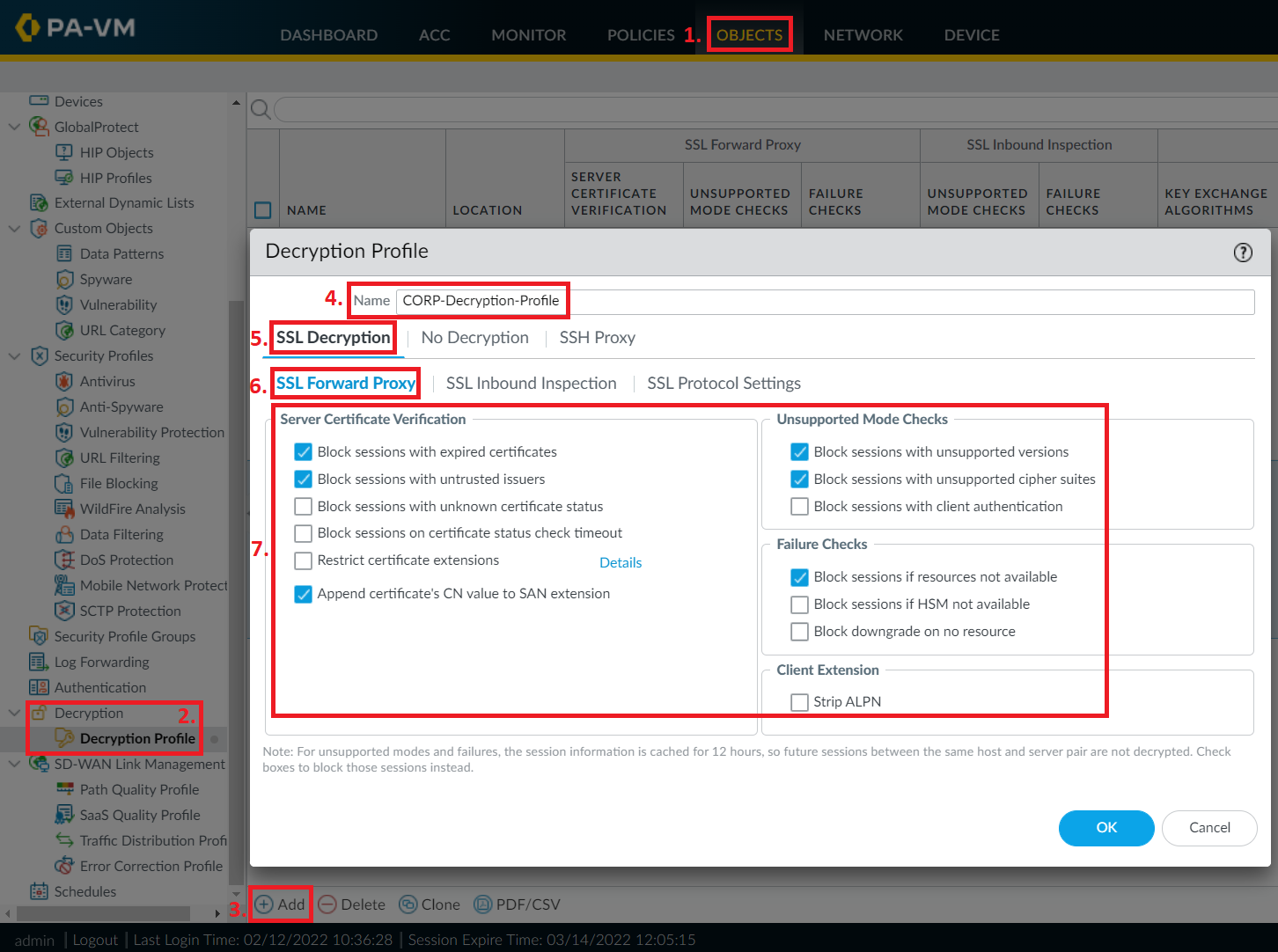
Navigate to the "Objects" tab and select "Decryption Profiles."
Create a new decryption profile or modify an existing one to enable SSL decryption.
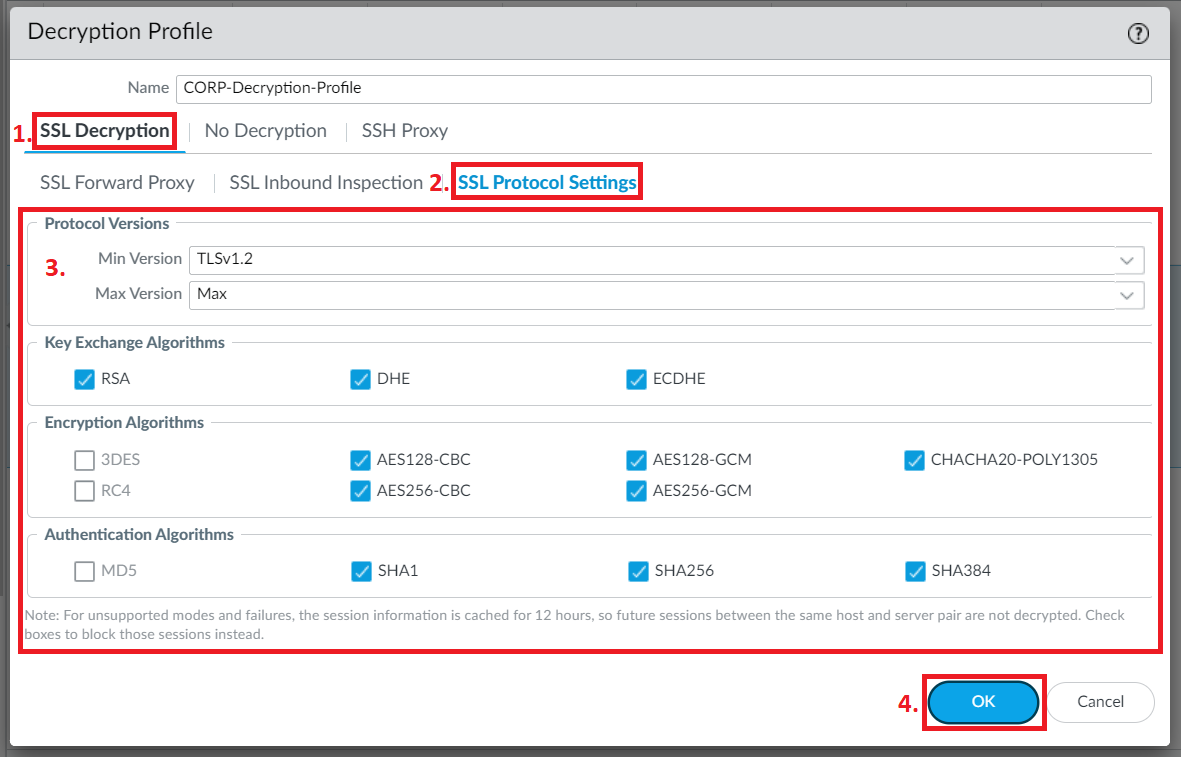
Specify the decryption policy settings, including SSL protocol versions, certificate verification options, and decryption exemptions if needed.
Step 2: Configure SSL Decryption Policies
Navigate to the "Policies" tab and select "Decryption."
Create a new decryption policy rule or modify an existing one to define the traffic to be decrypted.
Specify the source and destination zones, addresses, applications, and users for the decryption policy.
NOTE: SSL Decryption should be a slow rollout process to make sure business is not interrupted. A phased approach is considered best practice. Take a small group of users and decrypt a “low risk” URL category (ex. news, sports, etc)
Set the action to "decrypt" and apply the decryption profile created in the previous step.
Step 3: Manage SSL/TLS Certificates
Obtain and import SSL/TLS certificates into the Palo Alto NGFW for SSL decryption.
NOTE: Best practice is to use your company’s enterprise CA infrastructure to have the certificate signed. If you use a self-signed certificate from the firewall, each user will need it uploaded to their machine
NOTE: The firewall will have 2 certificates (one signed from the enterprise CA and one self-signed) uploaded/created. The signed certificate will be the Forward Trust cert and the self-signed cert will be the Unfrust. The Forward Trust cert will be the one used for the SSL Decryption process and the Untrusted cert will be the one the firewall responds with (to the user) if the “far end” website does not match the encryption/hash settings in the decryption profile - hence deeming it untrustworthy.
Ensure that the NGFW has the necessary root CA certificates to validate SSL certificates presented by servers during the decryption process.
Manage certificate revocation lists (CRLs) and OCSP responders to verify the validity of SSL certificates.
Step 4: Monitor SSL Decryption Traffic
Utilize the Palo Alto NGFW's monitoring tools to view decrypted traffic logs and analyze SSL decryption events.
Monitor SSL decryption performance metrics to ensure optimal firewall performance and identify any issues or anomalies.
Conclusion: Strengthening Network Security with SSL Decryption
SSL decryption is a critical security feature that enables organizations to protect against advanced threats hidden within encrypted traffic. By implementing SSL decryption on a Palo Alto Firewall following the steps outlined above, organizations can enhance their network security posture, mitigate risks, and ensure compliance with regulatory requirements. As cyber threats continue to evolve, SSL decryption remains an essential component of a comprehensive cybersecurity strategy, enabling organizations to stay ahead of emerging threats and safeguard their critical assets effectively.